Jul 08, 2010 Also the software is known as 'Real Crimes-Jack The Ripper', 'Real Crimes - Jack the Ripper', 'Real Crimes Jack the Ripper'. The most popular versions of the Real Crimes: Jack the Ripper are 12.0, 3.0 and 2.5. This software is an intellectual property of Gamers Digital, Inc. Our built-in antivirus scanned this download and rated it as 100% safe. With a brand new 3D printer, Andy set to work on designing Jack the Ripper Bot. The design has two trays mounted to a standard computer DVD drive, an ‘in’ tray and an ‘out’ tray. Assassin's Creed Syndicate - Jack the Ripper. Action & adventure. Blood, Drug Reference, Strong Language, Violence. Experience the chilling persona of Jack the Ripper, a killer who knows no boundaries while embarking on a campaign of fear and murder that threatens the very existence of the Brotherhood.
The jack the ripper software is developing at a frantic pace. New versions of the software should be released several times a quarter and even several times a month.
Home Search Games Tapes Covers Cheats Maps Software New Stuff Hall Of. Jack The Ripper: Category: Game/Adventure: Release Date: 2020-01-24: Language: English: Size. May 20, 2019 John the Ripper is free and Open Source software, distributed primarily in source code form. If you would rather use a commercial product tailored for your specific operating system, please.
Update for jack the ripper software.
There are several reasons for this dynamic:
First, new technologies are emerging, as a result, the equipment is being improved and that, in turn, requires software changes.
Secondly, the needs of users are growing, requirements are increasing and the needs are changing for jack the ripper software.
Therefore, it is necessary to monitor changes in the jack the ripper software and to update it in a timely manner.
/ If you do not update
JtR is primarily a password cracker used during pentesting exercises that can help IT staff spot weak passwords and poor password policies.
Here is the list of encryption technologies found in JtR:
How To Draw Jack The Ripper
- UNIX crypt(3)
- Traditional DES-based
- “bigcrypt”
- BSDI extended DES-based
- FreeBSD MD5-based (linux and Cisco IOS)
- OpenBSD Blowfish-based
- Kerberos/AFS
- Windows LM (DES-based)
- DES-based tripcodes
- SHA-crypt hashes (newer versions of Fedora and Ubuntu)
- SHA-crypt and SUNMD5 hashes (Solaris)
That’s the “official” list. JtR is open-source, so if your encryption of choice isn’t on the list do some digging. Someone might have already written an extension for it.
How to Download John the Ripper
JtR is an open-source project, so you can either download and compile the source on your own, download the executable binaries, or find it as part of a penetration testing package.
The official website for John the Ripper is on Openwall. You can grab the source code and binaries there, and you can join the GitHub to contribute to the project.
JtR is available on Kali Linux as part of their password cracking metapackages.
Tutorials for Using John the Ripper
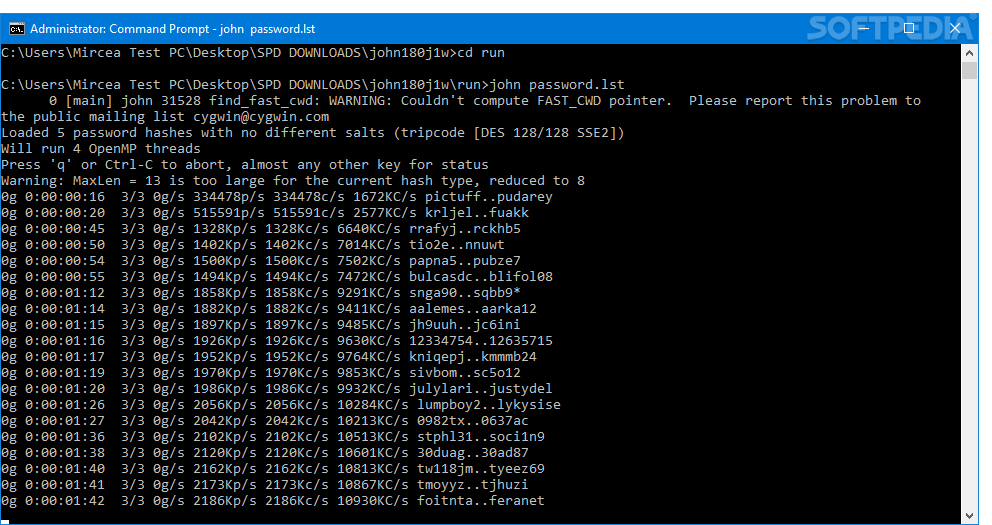
We are going to go over several of the basic commands that you need to know to start using John the Ripper. To get started all you need is a file that contains a hash value to decrypt.
If you ever need to see a list of commands in JtR, run this command:
Cracking Passwords
John The Ripper Software
John the Ripper’s primary modes to crack passwords are single crack mode, wordlist mode, and incremental. The single crack mode is the fastest and best mode if you have a full password file to crack. Wordlist mode compares the hash to a known list of potential password matches. Incremental mode is the most powerful and possibly won’t complete. This is your classic brute force mode that tries every possible character combination until you have a possible result.
The easiest way to try cracking a password is to let JtR go through a series of common cracking modes. This command below tells JtR to try “simple” mode, then the default wordlists containing likely passwords, and then “incremental” mode.
You can also download different wordlists from the Internet, and you can create your own new wordlists for JtR to use with the –wordlist parameter.
If you want to specify a cracking mode use the exact parameter for the mode.
Word Mangling Rules
Mangling is a preprocessor in JtR that optimizes the wordlist to make the cracking process faster. Use the –rules parameter to set the mangling rules.
Viewing Your Output
When you want to see the list of passwords that you have cracked, use the –show parameter.
Jack The Ripper Hacking Software
If your cracked password list is long, you can filter the list with additional parameters. You can also redirect the output using basic redirection in your shell. For example, if you want to see if you cracked any root users (UID=0) use the –users parameter.
Or if you want to show users from privileged groups use –groups.
Free Jack The Ripper Software
Below is the JtR command from our Live Cyber Attack Webinar. In this scenario, our hacker used kerberoast to steal a Kerberos ticket granting ticket(TGT) containing the hash to be cracked, which was saved in a file called ticket.txt. In our case, the wordlist used is the classic rockyou password file from Kali Linux, and the command was set to report progress every 3 seconds.
Jack The Ripper Dvd Software
If you want to see some cool pentesting and defense tactics using Varonis, check out the Live Cyber Attack Webinars! Pick any time that works for you!